Important News:SafeLogic Announces CryptoComply Go v4.0 with Comprehensive PQC Capabilities!! Read the announcement.
The Definitive Guide to FIPS 140-3 Validation & Certification
Understanding Federal Information Processing Standard 140-3
Federal Information Processing Standards Publication 140, Security Requirements for Cryptographic Modules, specifies the latest requirements for cryptographic modules utilized to protect sensitive but unclassified information. The National Institute of Standards and Technology (NIST) and the Canadian Centre for Cyber Security (CCCS) collaborate to run the Cryptographic Module Validation Program (CMVP), which assesses conformance to FIPS 140. NIST (through NVLAP) accredits independent testing labs to perform FIPS 140 testing. The CMVP reviews and validates modules tested against FIPS 140 criteria.
Validated is the term given to a module that has successfully gone through this FIPS 140 validation process. Validated modules receive a validation certificate that is posted on the CMVP’s website. Procurement agents will block the acquisition of products performing encryption by government agencies if the products do not have an active FIPS validation on the CMVP listing.
More information is available on the CMVP website.
Return to TOC

History of FIPS 140
Given the essential role cryptography plays in our digital world, it should be no surprise cryptography is the most highly regulated aspect of cybersecurity.

Return to TOC
FIPS 140-3, titled Security Requirements for Cryptographic Modules, is the third update to the FIPS 140 benchmark established by the National Institute of Standards and Technology (NIST) to specify security requirements for cryptographic modules and testing methodology for confirming conformance. FIPS 140-3 will eventually completely replace FIPS 140-2. Note that with FIPS 140, the -2 and -3 suffixes represent the second and third versions of the standard, not the second and third qualitative levels of security.
Return to TOC

What are the Four FIPS 140-3 Security Levels?
The FIPS 140-3 standard provides four increasing, qualitative levels of security: Level 1, Level 2, Level 3, and Level 4. These levels are intended to cover the wide range of potential applications and environments in which cryptographic modules may be employed. Each subsequent level builds upon the requirements of the previous level. These levels are clearly indicated on each validation certificate. The strength and functionality of the cryptography is the same for each level.
What Does FIPS 140-3 Cover?
The security requirements in FIPS 140-3 cover 12 areas:
-
Alignment with international standards ISO/IEC 19790:2012 and ISO/IEC 24759:2017
-
Module specifications
-
Module interfaces
-
Roles, services, and authentication
-
Software/firmware security
-
Operational environment
-
Physical security
-
Non-invasive security
-
Sensitive security parameter management
-
Self-tests
-
Life-Cycle assurance
-
Mitigation of other attacks
ISO/IEC 19790:2012 lists the security requirements for a cryptographic module utilized within a security system protecting sensitive information in computer and telecommunication systems. This International Standard defines four security levels for cryptographic modules to provide for a wide spectrum of data sensitivity and a diversity of application environments.
ISO/IEC 24759:2017 specifies testing requirements for cryptographic modules that provide a high degree of objectivity during the testing process and ensure consistency across testing laboratories.
Return to TOC
What is the Cryptographic Module Validation Program (CMVP)?
-
 The Cryptographic Module Validation Program (CMVP) is a joint effort between NIST and the Canadian Centre for Cyber Security (CCCS) that manages the FIPS 140-3 program.
The Cryptographic Module Validation Program (CMVP) is a joint effort between NIST and the Canadian Centre for Cyber Security (CCCS) that manages the FIPS 140-3 program. -
The program is open to any vendor that wants to have their cryptographic module tested and validated as being compliant with the FIPS 140 standards. Validated modules can be used by the US and Canadian federal governments, as well as other regulated industries.
-
CMVP testing is handled by independent Cryptographic and Security Testing Laboratories (CSTLs) that have been accredited by the CMVP.
-
Each CSTL submission is reviewed and validated by CMVP before the CMVP issues a FIPS 140-3 validation certificate.
-
The CMVP maintains a public listing of all FIPS 140 validated cryptographic modules. Government procurement agents use these listings to verify a vendor’s cryptographic module has successfully achieved FIPS 140-2 or FIPS 140-3 validation.
-
Procurement agents will block the acquisition of products performing encryption by government agencies if the products do not have an active FIPS validation on the CMVP listing.
Return to TOC
-
As the CMVP indicates:
-
“FIPS 140-2 and FIPS 140-3 requirements are applicable to all U.S. Federal agencies. Agencies must use cryptographic-based security systems to provide adequate information security for all operations and assets as defined in 15 U.S.C. § 278g-3.
-
Non-validated cryptography is viewed as providing no protection to the information or data—in effect the data would be considered unprotected plaintext. If the agency specifies that the information or data be cryptographically protected, then FIPS 140-2 or FIPS 140-3 is applicable. In essence, if cryptography is required, then it must be validated. Should the cryptographic module be revoked, use of that module is no longer permitted."
-
-
For companies selling to the public sector, it is essential to prove their solutions use FIPS validated cryptography anywhere they use encryption.
-
Whether for FedRAMP, CMMC 2.0, Common Criteria, DoDIN Approved Product List (APL), StateRAMP, FISMA, NIST SP 800-171, or other compliance regimens, the NIST FIPS 140 standard is typically a requirement for any cryptography used in the solution.
-
Clearing the FIPS 140 validated cryptography requirement can often mean the difference between making the sale or not.
-
Third-party assessment organizations (3PAOs) and public sector procurement officers will examine the evidence for the use of FIPS 140 validated cryptography. That usually entails searching NIST’s Cryptographic Module Validation Program (CMVP) list for proof of an active certificate that corresponds to the FIPS 140 validated module that a company purports to use. They will examine these certificates and their accompanying security policies for various important details.

Return to TOC
The FIPS 140-3 Validation Process is Time-Consuming, Frustrating and Costly
As mentioned elsewhere in this document, the traditional approach to achieving FIPS 140-3 is lengthy, costly, unpredictable, distracting, and ongoing. This process can take two+ years, not counting the time required to develop the cryptographic software and supporting documentation and tools.
Going for FIPS 140-3 validation on your own is definitely not for the faint of heart. But this is not the only option. SafeLogic’s unique FIPS Validation-as-a-Service will get you a FIPS 140-3 certificate in your own company’s name in just two months versus the two years it normally takes. Learn more about SafeLogic's FIPS Validation-as-a-Service.
Return to TOC

FIPS 140-3 Validation is Not “One-and-Done”

FIPS 140 validation is not a one-and-done project. Instead, it is a process that a submitter must manage over the entire lifetime of their FIPS 140-3 certificate. New FIPS 140-3 certificates usually have an expiration date five years into the future. Hence, the submitting organization may conclude it has “solved” the FIPS 140 validation problem for that timeframe. That is not the case.
-
FIPS 140 requirements constantly change. For example, algorithms become disallowed, approved key sizes change, and new algorithms become allowed. The FIPS requirements change as computing capacity increases, as do the cryptanalytic techniques that adversaries have at their disposal.
-
In practice, at least every year, there are “transitions” in standards requirements. For some of these transitions, creators of FIPS 140 validated modules need to make changes to their modules and associated documentation so that their modules will not move to “Historical”. Modules and associated documentation then need to go through the process of being reviewed and tested by the laboratories, and then they go through another CMVP review.
-
If an organization fails to keep up with the status of the FIPS standards, their certificate may not survive the transition and will become what is known as “historical.” These certificates are no longer active and cannot be used for any new acquisitions by government agencies.
-
For example, there was a transition in 2022 that roughly 50% of previously active FIPS 140 validated modules did not survive. This shortened their useful lives, in many cases to far less than their theoretical five-year sunset dates.
-
Submitters must keep spending time and money on an ongoing basis to remain FIPS 140 validated. As difficult as achieving initial FIPS 140 validation may be, maintaining it over time is even more difficult.
In contrast, the MaintainCert component of SafeLogic's FIPS Validation-as-a-Service ensures your FIPS 140-3 certificates remain in Active status through their lifetime, despite any changes to the FIPS 140-3 standard. Learn more about SafeLogic’s MaintainCert.
Return to TOC
FIPS 140-3 Compliant is not FIPS 140-3 Validated
As we wrote about in a recent blog post, compliant, validated, and certified are NOT synonyms when it comes to FIPS 140-3. Thinking they are can lead to very expensive mistakes.-
Validated means your company's cryptographic module has passed a formal testing process with a NIST-approved lab and received a FIPS validation certificate in your company’s name. This certificate is listed publicly.
-
Some organizations think they can avoid the whole FIPS 140 validation hassle by using a FIPS 140 validated cryptographic module from an open-source, OS or cloud services provider. Such a strategy is called ‘FIPS compliant’ or ‘FIPS inside’. While this might seem like a good idea, this FIPS compliance strategy is extremely risky for two reasons.
-
First, FIPS compliant today may not be FIPS compliant tomorrow if someone else’s module goes out of compliance (e.g., goes Historical). This often happens when a vendor declares an older product ‘end-of-life’. When that happens, it’s your public sector sales that are at risk.
-
Second, government procurement agents may block the acquisition of products that do not have FIPS certification in their own name in the CMVP database. They will want to see that the CMVP certificate has an organization’s specific details. Without that being the case, it may be challenging to demonstrate that an organization is actually using the FIPS 140 validated module in its solution, and using it as intended.
SafeLogic's FIPS Validation-as-Service customers don't have these challenges. Their FIPS 140-3 validated CryptoComply-based modules get FIPS 140-3 certificates and listings in the CMVP database in their company's name. And it takes just two months, not two years! Then SafeLogic maintains the software and their certifications, ensuring they remain in Active status until their sunset dates.
Return to TOC

Only SafeLogic's Unique FIPS Validation-as-Service Expedites and Maintains Your FIPS 140-3 Validation Over Time
Getting your own cryptography software reviewed, tested, validated, and certified by NIST can take as long as two years, not counting the time required to develop the software. SafeLogic literally cuts the time required to achieve NIST certification from two years to two months, then keeps your certification active over time with these three key FIPS Validation-as-a-Service capabilities.

CryptoComplyTM
CryptoComply is SafeLogic’s flagship software, a family of FIPS 140 validated cryptographic software modules. They deliver “Drop-in Compliance” as direct replacements for popular open-source crypto providers.

RapidCertTM
SafeLogic revolutionized the FIPS industry twelve years ago with RapidCert, the industry's first expedited rebranding program. Get FIPS certification of your CryptoComply solution, in your name, in only two months with RapidCert.


MaintainCertTM
Now SafeLogic is revolutionizing FIPS again with MaintainCert. FIPS certificates go ‘historical’, meaning they are no longer valid, all the time. Not with MaintainCert, SafeLogic’s new white-glove support service.
CryptoComply Achieves FIPS 140-3 Validation for 28 Operating Environments (OEs)
SafeLogic is excited to announce that its CryptoComply v3 encryption software has achieved FIPS 140-3 validation, has received FIPS 140-3 certificate #4781 from the National Institute of Standards (NIST), and is now Generally Available (GA)
CryptoComply v3 is certified across more than two dozen OEs, from mobile operating systems (e.g., iOS, iPadOS, and Android), to Windows, macOS, Windows Server, Oracle Solaris, and several Linux distributions (e.g., AlmaLinux, Debian, FreeBSD, Red Hat Enterprise Linux, Rocky Linux, SUSE Linux, and Ubuntu).
Learn more about CryptoComply.
Return to TOC

The FIPS 140-3 Transition for SafeLogic Customers
-
CryptoComply v3 has achieved FIPS 140-3 validation for 28 operating environments
-
SafeLogic expects to receive FIPS 140-3 validation for CryptoComply for Java in Q4 2024
-
FIPS 140-3 Rebranding support from CMVP is expected in late 2024
-
SafeLogic FIPS 140 Validation-as-a-Service customers receive 140-3 at no additional cost as part of their subscriptions
-
Current CryptoComply customers have options on the timing of upgrading to SafeLogic's new FIPS 140-3 validated modules
-
SafeLogic is working with its 140-2 customers to get them migrated 140-3 in a smooth and orderly manner
-
SafeLogic continues to support and provide FIPS 140-2 validated modules and certificates for its clients
-
SafeLogic continues to keep its clients’ FIPS 140-2 certificates in Active status
-
Procurement officers do not care whether you have a FIPS 140-3 or 140-2 certificate as long as you have an Active certificate in your company’s name (i.e., you’re FIPS 140 validated)

Return to TOC
How is FIPS 140-3 Different from FIPS 140-2?
FIPS 140-3 introduces several significant changes and enhancements over its predecessor:
-
Alignment with ISO/IEC 19790:2012 and ISO/IEC 24759:2017 By aligning with these international standards for cryptographic modules and testing methods, FIPS 140-3 ensures global interoperability and recognition of validated cryptographic modules worldwide. These international standards were developed by the international community from FIPS 140-2.
-
Enhanced Physical Security Requirements FIPS 140-3 provides more detailed and stringent requirements for physical security, particularly at higher security levels. This includes better protection against environmental attacks and unauthorized physical access.
-
Improved Key Management Practices The updated standard places greater emphasis on secure key management practices, ensuring that cryptographic keys are generated, stored, and destroyed securely.
-
Increased Focus on Software Security With the growing prevalence of software-based cryptographic modules, FIPS 140-3 introduces more comprehensive requirements for software security. This includes secure coding practices, regular software updates, and protection against software vulnerabilities.
-
Updated Testing and Validation Processes The testing and validation processes have been updated to reflect the latest advancements in cryptographic technology and security testing methodologies. This ensures that validated modules meet the highest security standards.
| FIPS 140-2 Requirement Areas | FIPS 140-3 Requirement Areas |
| Cryptographic Key Management | General |
| Cryptographic Module Ports and Interfaces | Cryptographic Module Specification |
| Cryptographic Module Specification | Cryptographic Module Interfaces |
| Design Assurance | Roles, Services, and Authentication |
| EMI/EMC | Software/Firmware Security |
| Finite State Model | Operational Environment |
| Mitigation of Other Attacks | Physical Security |
| Operational Environment | Non-Invasive Security |
| Physical Security | Sensitive Security Parameter Management |
| Roles, Services, and Authentication | Self Tests |
| Self Tests | Life-Cycle Assurance |
| Mitigation of Other Attacks |
For more information on the differences between FIPS 140-3 and FIPS 140-2 for Level 1 software modules, see this recent blog post from SafeLogic.
Return to TOC
-
Short term, the biggest challenge the industry faces is the transition from FIPS 140-2 to FIPS 140-3.
-
All FIPS 140-2 certificates still active as of September 2026 will move to the historical list at that time, meaning virtually the entire industry needs to transition to FIPS 140-3 by then.
-
With FIPS 140-3, NIST has raised the bar on the software, documentation, testing, and laboratory procedures required to counter new and emerging security threats.
-
For cryptographic module suppliers, the already daunting 2+ year FIPS 140 validation process has gotten even longer, harder, and more complex.
-
With a large backlog of FIPS 140-3 validations in the NIST CMVP queue, NIST made some important structural changes, such as rolling out automation to identify non-conformances and thus move the review process along more quickly.
-
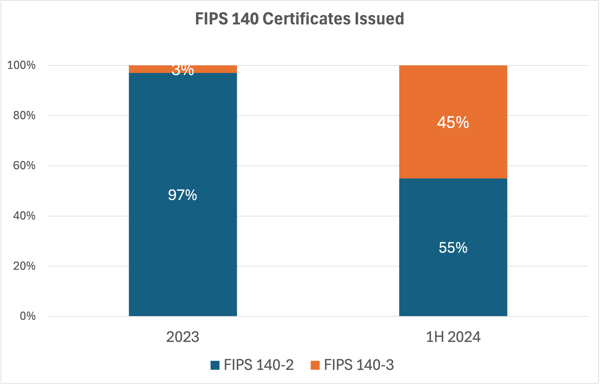
These and other changes appear to be working. While FIPS 140-3 only made up 3% of the FIPS 140 certificates issued in 2023, FIPS 140-3 made up 45% of those issued in the first half of 2024.
Return to TOC
What is Required to Get FIPS 140-3 Validated?
What are the steps in the FIPS 140-3 validation process?
 Traditional FIPS 140 validation is time-consuming, frustrating, and costly. Getting a FIPS 140 certificate has three main phases: documentation, testing, and validation. This process can take two+ years, not counting the time required to develop the cryptographic software and supporting documentation and tools. The process requires extensive collaboration between your developers, product managers, compliance experts, a FIPS consultant you hire, a NIST-authorized certification lab, and NIST itself.
Traditional FIPS 140 validation is time-consuming, frustrating, and costly. Getting a FIPS 140 certificate has three main phases: documentation, testing, and validation. This process can take two+ years, not counting the time required to develop the cryptographic software and supporting documentation and tools. The process requires extensive collaboration between your developers, product managers, compliance experts, a FIPS consultant you hire, a NIST-authorized certification lab, and NIST itself.
The validation phases are:
-
Implementation Under Test – evidence and module have been submitted to the testing lab, and testing is underway.
-
Testing includes a conformance review of the module, a review of all documentation, algorithm testing through NIST’s CAVP program (ACVP testing), entropy testing (if applicable), operational testing, and the creation of the lab report. All of the phases are typically iterative.
-
-
Review Pending – testing has been completed and the lab report has been submitted to CMVP awaiting review.
-
In Review – A member of CMVP has been assigned and has begun the review of the lab report.
-
Coordination – Questions from CMVP have been sent back to the test lab. Responses from the lab are then sent back to CMVP.
-
Finalization – All questions have been satisfactorily addressed and the FIPS certificate is prepared for issuance.
If successful, the submitted module will be FIPS 140 validated, and NIST will issue a CMVP certificate. The issued certificate will include a sunset date, which is the lifetime of the FIPS certificate. This is usually five years for a new submission. However, there is no guarantee that the certificate will remain active until sunset without significant additional effort.
Getting your own FIPS 140-3 certificate is not for the faint-of-heart. Fortunately there is an alternative. You can join the 100+ technology leaders who have chosen to partner with SafeLogic to obtain a FIPS 140-3 certificate in just two months, not two years.
Return to TOC
What Does it Cost to Get FIPS 140-3 Validated?
FIPS Consultants
Vendors may choose to hire outside consultants to prepare the necessary documentation and tools for the module testing, or to advise on conformant designs. These consultants will charge the vendor their fees for this service.
Laboratory Fees
CMVP-accredited Cybersecurity and Security Testing (CST) laboratories charge a fee for the testing of a cryptographic module. Testing time, scope and cost vary depending on many factors, including the following:
- Cryptographic module type – software, firmware, hardware
- Overall security level of the cryptographic module – 1, 2, 3, or 4
- Functionality of the module – e.g. supported algorithms and services
- Number of environments listed on the certificate – e.g. multiple tested operating systems
- Type of validation submission – e.g. new submission, major update, or CVE fix.
- Accuracy and completeness of documentation package
- Support needed for testing tools for algorithm testing or operational testing
- The number of deficiencies identified by a laboratory during the conformance testing process.
NIST and CCCS do not get involved in the contract negotiations between the vendor and a lab. This is to ensure the independence of the validation authorities.
NIST Cost Recovery Fees
Cost recovery is a fee charged by NIST's CMVP program for FIPS module validations and updates. A nominal fee is charged to recover the costs for the validation tasks and the program management responsibilities performed by the CMVP.
The CMVP fee structure is updated annually. The current fee structure is effective 1/1/2024 and is subject to change to reflect actual operating costs:
- Security Level 1: Base fee: $14,000
- Security Level 2: Base fee: $15,000
- Security Level 3: Base fee: $15,500
- Security Level 4: Base fee: $17,000
Note the above fees only cover the NIST fee the first time a vendor attempts to get a cryptographic module FIPS 140-3 validated. They do not include the cost of developing and maintaining the software, nor do they include the ongoing cost of potential revalidations to keep a FIPS 140-3 certificate in Active status.
In contrast to the budgetary black hole that initial and ongoing FIPS 140-3 validation can represent, SafeLogic’s FIPS Validation-as-a-Service provides FIPS 140-validated cryptographic modules, rapid delivery of a FIPS 140 certificate in your company’s name, and ongoing software and certificate support for a predictable, affordable cost.
Return to TOC
The CMVP is constantly working to improve the security of FIPS 140-3 validated cryptographic modules and the efficiency and effectiveness of the CMPV testing and validation program. The two most obvious changes in the FIPS program were the transition from FIPS 140-1 to FIPS 140-2 and the transition from FIPS 140-2 to FIPS 140-3.
However, FIPS requirements are constantly changing, even within the context of FIPS 140-3. The FIPS 140-3 bar will go even higher soon with new PQC (post-quantum cryptography) algorithm support and requirements for Entropy Source Validation (ESV).
Return to TOC

Post-Quantum Cryptography
On August 13, 2024, NIST announced the publication of its first post-quantum cryptography (PQC) algorithm standards:
-
ML-KEM for key encapsulation
-
ML-DSA for digital signatures
-
SLH-DSA for digital signatures
Publishing the FIPS standards for the PQC algorithms was a crucial step, but not sufficient for these algorithms to be included as approved algorithms in FIPS 140-3 modules. Fortunately, along with the algorithm announcement, the CMVP updated its standards and tooling. With these CMVP updates, all the pieces are now in place to start designing and testing FIPS 140-3 modules with approved PQC algorithms! SafeLogic is hard at work, and we look forward to offering one of the first FIPS 140-3 validated modules with PQC algorithms!
Learn More About SafeLogic’s PQC solutions
Return to TOC
New Requirements for Entropy Sources
Another great example of NIST continuously raising the security bar (and FIPS 140-3 requirements for cryptographic module providers) is entropy source validation. Cryptographic modules use entropy sources to generate random numbers. If the entropy source is not secure, the keys the module produces will not be secure either.
The CMVP has gradually increased entropy requirements over the years. Initial entropy requirements were limited to rudimentary self-tests and entropy source descriptions.
The entropy requirements are now much more mature. All FIPS modules must implement an entropy source or provide a strong justification for why this source is not applicable. Entropy sources must meet the requirements of SP 800-90B; these requirements often require design changes. And entropy sources must go through the CMVP’s entropy validation subprogram as part of the FIPS module validation:https://csrc.nist.gov/Projects/cryptographic-module-validation-program/entropy-validations
The CMVP also continues to expand the applicability of the entropy requirement. By 2026, all software modules will need to meet the entropy requirements if they use entropy from the operating system or hardware platform.
Keep an eye on the SafeLogic blog for updates on NIST's new FIPS 140-3 entropy requirements.
Return to TOC
Implementation Guidance Updates
The CMVP provides continual updates on the latest guidance through the FIPS 140-3 Implementation Guidance (IG), which can be found at the following link: https://csrc.nist.gov/Projects/cryptographic-module-validation-program/fips-140-3-ig-announcements
Return to TOC
FIPS 186-5 Digital Signature Standard
The algorithm standards approved in FIPS 140-3 are continually updated. Recently the digital signature standard was updated from “FIPS 186-4” to “FIPS 186-5”. The CMVP implemented a corresponding transition. Because of this transition, new submissions to the CMVP after February 4, 2024 must now align with FIPS 186-5 instead FIPS 186-4.
Return to TOC
SHA-1 Transition
While SHA-1 has been disapproved in FIPS modules in many contexts, it is still approved in some contexts. NIST will completely disallow the use of SHA-1 on December 31, 2030:
https://csrc.nist.gov/news/2022/nist-transitioning-away-from-sha-1-for-all-apps
Return to TOC
Revisions to FIPS 140-3
The international standards that FIPS 140-3 references go through a continual revision process. As these standards are updated, the FIPS 140 program will also incorporate these changes.
Return to TOC

